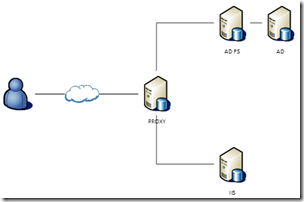
One of our customers that is using Master Data Services in an environment provided by us, requested the possibility for the users to log on using their Office 365 credentials. For most web applications this is fairly simple, but the MDS Web service is not a claims-aware application. MDS uses Integrated Windows authentication and authorization based on the user’s Active Directory Account.
For users inside your organization this can be solved by using a reverse proxy. The Web Application Proxy service in Windows Server 2012 can provide pre-authentication for non-claims aware applications published with Integrated Windows Authentication (IWA) using Kerberos
When using an external claims provider this is no longer possible; the claims provided by this AD FS can’t be used for delegation.
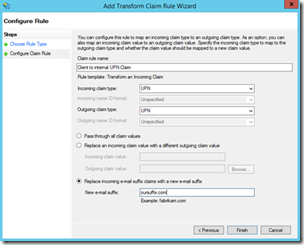
AD FS provides us with the tools to fix this. In the AD FS Management console we can map the claims provided by the customer and map those to claims the Proxy Server can use to do the delegation. The only information it actually needs is the UPN Claim.
With the “Add Transform Claim Rule Wizard” we are able to map the incoming UPN claim (firstname.lastname@customersuffix.com), to the UPN claim that we would be able to provide in AD (firstname.lastname@oursuffix.com):
If this doesn’t suit your needs you can configure Custom Claim Rules to do more complex operations and even do look-ups in a custom attribute store!
When a client now logs in, the UPN claim is transformed to a claim the proxy server can use for delegation.
If our AD contains a user with UPN firstname.lastname@oursuffix.com we can do Integrated Windows Authentication using Kerberos on our MDS Web Application.
I would not advise this setup if a large number of users are needed and need to be manually created and managed. But for a small number of user it seems to be a good work-around. Depending on the scenario you can also map a group (or other) claim to a user claim to limit the manual work.
Let us know what you think and what issues you encountered. Also let us know of any alternatives for a scenario like this you might have.
Subscribe to our RSS feed