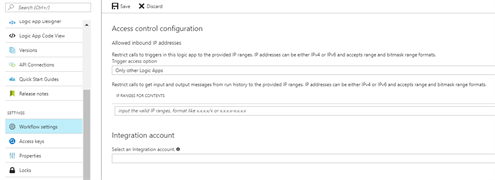
Runtime restrictions
You can configure IP restrictions to your Logic Apps triggers:
- Any IP: the default setting that does not provide any additional security
- Only other Logic Apps: this should be the default setting for Logic Apps that are used as reusable components
- Specific IP ranges: this should be configured for externally exposed Logic Apps, if possible
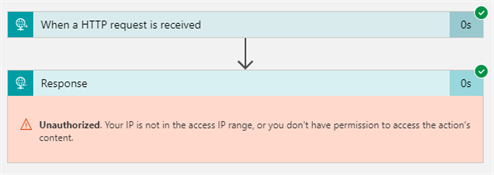
When trying to access the Logic App trigger from an unauthorized IP address, you get a 401 Unauthorized.
“The client IP address ‘XXX.XXX.XXX.XXX’ is not in the allowed caller IP address ranges specified in the workflow access control configuration.”
Run history restrictions
You can also restrict calls to the run history inputs and outputs. When there are no IP addresses provided, there’s no restriction. From the moment you provide IP ranges, it behaves as a whitelist of allowed addresses.
When trying to access the Logic App run details from an unauthorized IP address, you can still see the visual representation of the Logic App run. However you’re not able to consult the further details.
Conclusion
Another small, but handy security improvement to Logic Apps. It’s important to be aware of these capabilities and to apply them wisely.
Cheers!
Toon
Subscribe to our RSS feed