In short: no matter what which identity provider (AAD, Google, Twitter, etc..) is used to sign up, when the user belongs to the @codit.eu domain it should be added to the “Codit Dev Team” custom group.
The basic idea here is to use logic apps as a batch process to get the list of registered users and then call a child logic app to assign the current developer to a proper custom group to manage the product visibility.
Logic Apps and Azure API Management
There are three ways to invoke an API Management endpoint from a Logic App:
- API Management connector. The connector is pretty straightforward. You first select an APIM tenant, the API and then the operation to be called. Finally, the available headers and parameters are automatically displayed. The APIM connector by default shows only the APIM tenants created in the same subscription where the Logic App was created.
- Http + Swagger connector. This connector provides a similar user experience as the APIM connector. The shape of the API with the parameters are automatically integrated in the designer.
- Http connector. It requires to specify HTTP verb, URL, Headers and Body to perform an HTTP call. Simple as that!
In this exercise, all the services that had been integrated are located in different Azure subscriptions therefore I used only Http and Http+Swagger connectors.
Manage ’em all
With the “Every API should be a managed API” mantra in mind and with the final goal to have a more information about which API is called and its performance we created a facade API for every HTTP call.
Here the list of managed APIs:
- Every call to the Azure Resource Manager (get users, get groups by user, add user to group)
- Get the token to authorize the ARM call
- Call the child Logic App
And here the Logic App workflows that had been created.

Some other benefits we got from the virtualization:
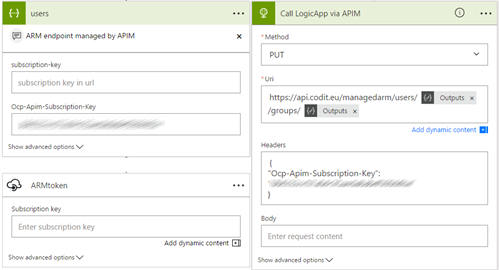
- Use of a single authorization model between Logic App and APIM by providing an API Key via the “Ocp-Apim-Subscription-Key” header.
- Balancing complexity and simplicity. The ARM authentication is delegated to the API Management layer.
- Apply a consistent resource naming convention.
Azure API Management Policies
The policy engine is where the core power of Azure API Management lies. Let’s go through the policies that have been configured for this exercise.
Get the bearer token
A token API with a GET operation is used by the ARM facade API to get the bearer token to authorize the call to Azure Resource Manager endpoint. The policy associated to the “get-token” operation changes the HTTP request method and sets the body of the request to be sent to the AAD token endpoint using the password flow.
Call the ARM
This is the call to the ARM endpoint (get users, get groups by user, add user to group). The “send-request”-policy is used to perform a call to the private token API and to store the response in the bearerToken context property.
The “set-header” policy in combination with a policy expression is used to extract the token and to add it as a header to the request sent to the ARM endpoint.
This policy can be improved by adding the policy expressions to store and retrieve the token from the cache. Here an example.
Logic Apps facade API
The Logic Apps workflows that expose an HTTP trigger call can be called by using the POST verb only and passing the parameters in the body of the request.
The child workflow that takes care to assign a user to a specific group has been virtualized via Azure API Management to change the URL segments as here https://api.codit.eu/managedarm/users/{uid}/groups/{groupname} and to change the request method to PUT.
Conclusion
Thanks to this simple Logic App and some APIM power I can now be sure that every new colleague that sign up to our developer portal is automatically associated to the internal developer team so that he/she can get access to a broader set of APIs.
A similar result can be achieved using the Azure B2B/B2C integration in combination with the AAD security groups but, at the time of writing, the APIM integration with AAD B2C has not been completed yet.
Another benefit of managed APIs is the gain of visibility of the exposed assets and their performance. Discover how an API is used, information about the consumer and be able to discover the trends that are most impacting the business.

Cheers
Massimo
Subscribe to our RSS feed