Introduction
In an era dominated by digital transformation, the cloud has emerged as the backbone of innovation and efficiency. However, as organizations increasingly rely on cloud services, concerns regarding data sovereignty and security have taken center stage.
Recognizing the need for a secure and compliant cloud environment, Microsoft provides several components to tackle these issues.
Azure has introduced Azure Sovereign Cloud, as well as Microsoft Cloud for Sovereignty (MCfS) & Confidential Compute. What does each component mean and how should you work with them? You’ll find out in this blog post!
Note: for readability, Microsoft Cloud for Sovereignty will be called MCfS later in this blog post.
Understanding Azure Sovereign Cloud
Azure Sovereign Cloud is a specialized cloud offering designed to meet the unique requirements of government agencies, critical infrastructure providers, and other entities with specific data sovereignty needs. It is an extension of the Azure cloud platform but is distinct in its dedication to addressing regulatory, compliance, and data residency requirements.
Azure Sovereign Cloud is a specific Azure Region that works differently from all other regions already available. It ensures that compute & data remain within the region and provides logical redundancy. These clouds are disconnected from the main Azure stream and are not always maintained by Microsoft itself.
At the time of writing, there are only two active regions working like this: one in China & one in the US.
These regions come with a lot of extra complexities. You are really disconnected, and the region needs to be managed as a full Azure Region, with all of the extra management of security, compliancy, constraints, and more.
A concrete example: Azure Service upgrades need to be installed by the Sovereign region itself, which are based on the capacity & availability of that service in that region.
Luckely, it doesn’t need to be so drastic
However, Microsoft sees that there are other approaches to reaching similar sovereignty levels. Say hello to “Microsoft Cloud for Sovereignty” (MCfS).
MCfS is a solution from the CAF (Cloud Adoption Framework) which defines a set of rules, requirements and policies etc. which enable you to be as secure as possible, without having the ability to leak any information to anyone (even the cloud service provider).
What Microsoft can do and has done, and the location of service reliability issues, is all shared via the Transparancy Logs. This gives you sovereignty in data residency so that your data doesn’t leave the region, while still enabling redundancy.
Last but not least, it provides Sovereign controls to monitor your level of compliancy, and provides you with an easy way to do governance on the whole platform.
Another big difference is that you can run it on any Azure Region.
Landing zones
MCfS is basically an Enterprise Landing zone, onto which customers can onboard.
This consists of multiple components:
- “Sovereign Landing Zone” (SLZ), which is available on GitHub (for the policies and rules).
- “Transparancy Logs“, to gain insights into the Microsoft interactions inside your subscription
- “Workload Templates” with real-life examples for faster integration & understanding, also available in its own GitHub repo.
On an interesting note: the SLZ shares the same fundamentals with the Codit Landing Zone. For more information on this, click here.
And so where does “Confidential Compute” fit?
While Azure Sovereign Cloud & MCfS focus on network & security (data-in-transit), storage (data-at-rest) and governance of your application landscape, Confidential Compute covers the other side of the story.
Confidential Compute makes sure that the process you are running is running in a secure environment, where no one can read/see what is going on in your process. (= data-in-use).
That being said, Confidential Compute can be provided in several forms:
- SQL Azure Always Encrypt
- Confidential Containers on AKS
- Confidential Containers on Azure Container Instances
- Confidential VM’s
- …
In all scenarios, the only objective is that no one, except you, can see the data in its raw, valuable form.
Here’s how Confidential Compute functions work:
- Isolation of Sensitive Workloads: Confidential Compute utilizes hardware-based security measures, such as Trusted Execution Environments (TEEs) or enclaves, to create isolated environments for processing sensitive workloads. This ensures that data remains confidential and secure from potential threats.
- Secure Communication: Government agencies and critical infrastructure providers often need to collaborate on projects without compromising sensitive information. Confidential Compute allows secure collaboration by enabling multiple parties to work on encrypted data without exposing the actual content.
- Protecting Against Insider Threats: Confidential Compute mitigates the risk of insider threats by restricting access to sensitive data even for administrators or cloud service providers. The encrypted nature of the enclave ensures that only authorized entities can access and process the data.
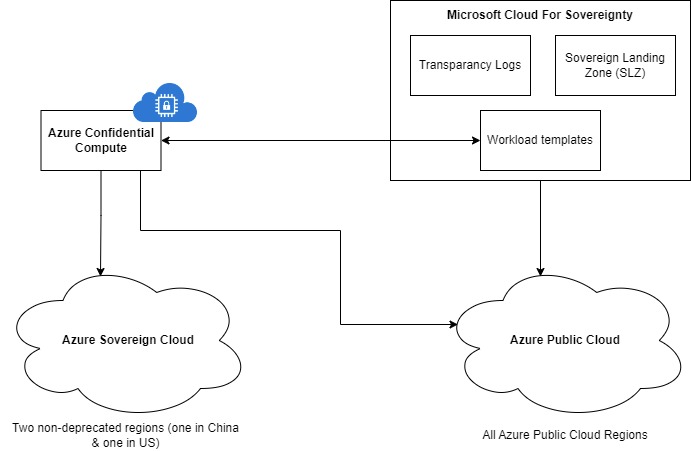
Visual overview
Images speak more than words, so let’s visualize what we just described:
Conclusion
In an age where data sovereignty and security are non-negotiable, it is important to be aware of all of these new trends & insights.
Azure Sovereignty already provides standardized robust guardrails for highly regulated industries and the public sector, while Confidential Compute elevates the platform’s security capabilities, providing a secure enclave for processing sensitive workloads.
All of this happens while you are still able to use the power of the cloud. At the same time, meeting regulatory requirements also sets a new standard for safeguarding sensitive information in the cloud.
A lot is still taking shape in this area. Codit can help you to implement this secure platform for the future, protecting both your today and tomorrow.
Hope you enjoyed this read,
Gillian
Abonneer je op onze RSS feed