Usually, the difficulty is not in the API itself (which is well documented, see Microsoft Learn), but getting the prerequisites right while avoiding potential pitfalls along the way.
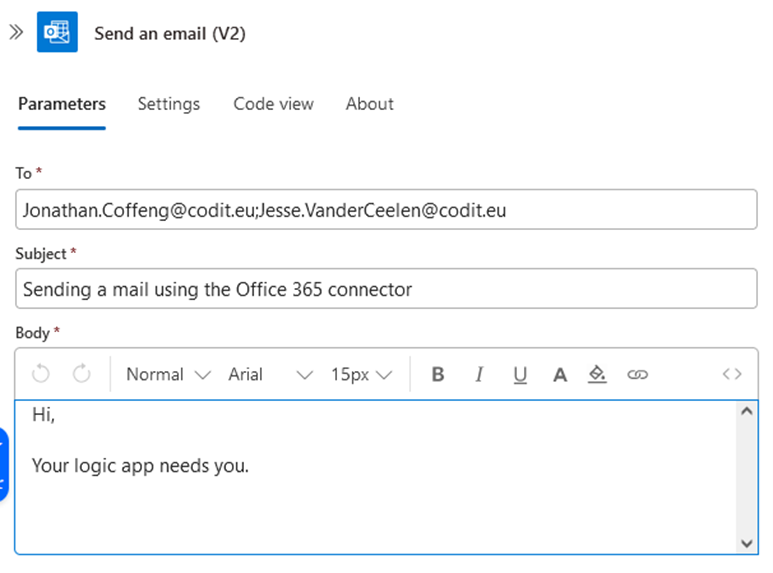
In short you need the following:
- A sys admin with Azure Admin permissions (and Exchange Online Admin permissions), which you only need once (and not each time like with a Logic App connector).
- App registration with Mail.Send application permission (see caveat below).
- User / mailbox with Microsoft 365 license
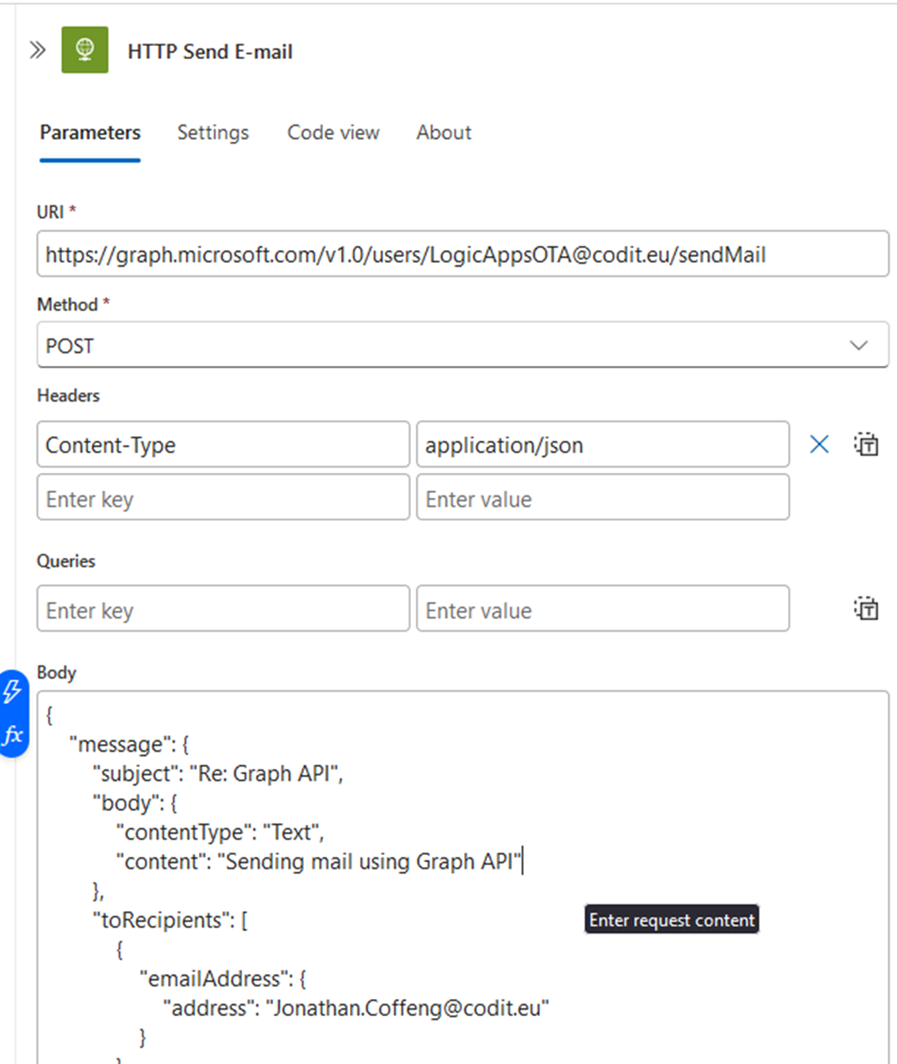
Setting Up In Logic Apps
In the screenshot below, you will see how to set up the connection using the HTTP connector. There is one POST endpoint with the Sender specified (in this case LogicAppsOTA@codit.eu), the body can either be json or a full MIME message (in which case Content-Type header changes to text/plain).
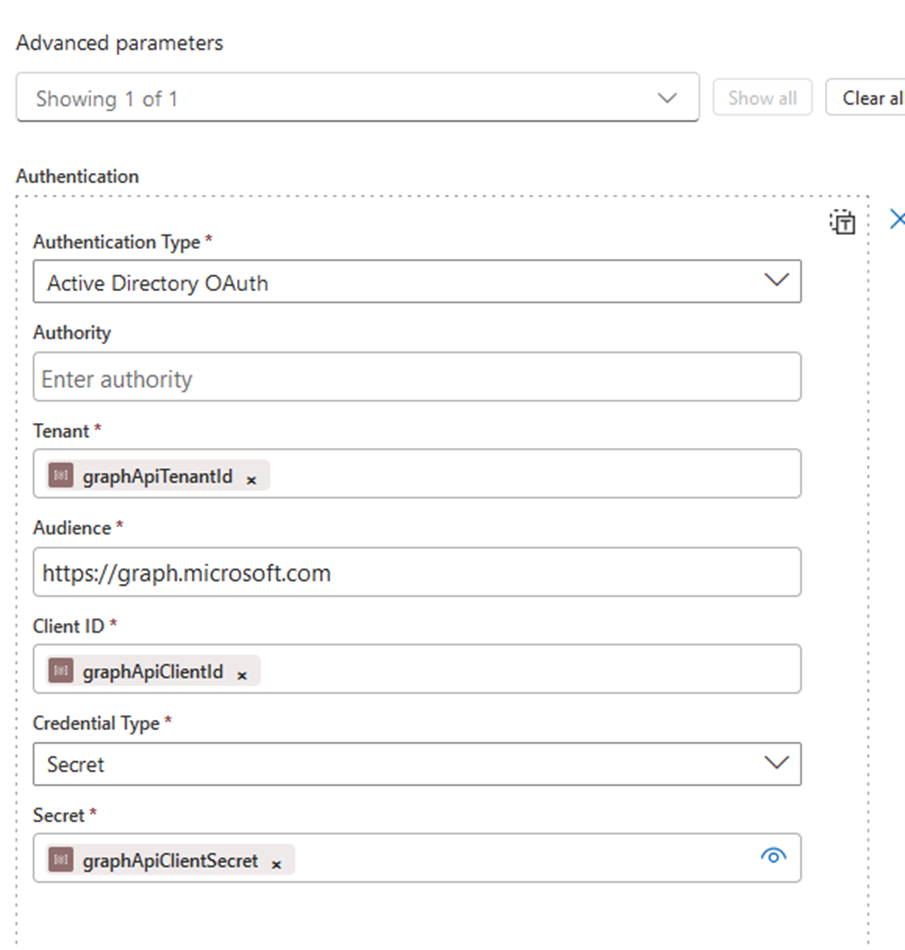
The following image shows how to set-up the authentication using Azure Active Directory OAuth (connecting to the app registration with the Mail.Send permission).
All in all, it is slightly more involved than the standard Office 365 connector, but it gives the following benefits:
- User interaction to refresh or connect to Office 365 e-mail account is no longer necessary
- Sender can be dynamic (no longer tied to user setting up connection)
- More options in sending e-mail (MIME, json)
- Potential re-usage of Graph API in other ways
Subscribe to our RSS feed