The Microsoft Product team is constantly adding features to the service, recently conditional policies have been added.
Policies overview
Policies can be applied at different scopes (Global, Product, API, and Operation), some are allowed only on the inbound channel, some others on the contrary only on the outbound.
The table summarizes the policies as today with their scope and the applicability.
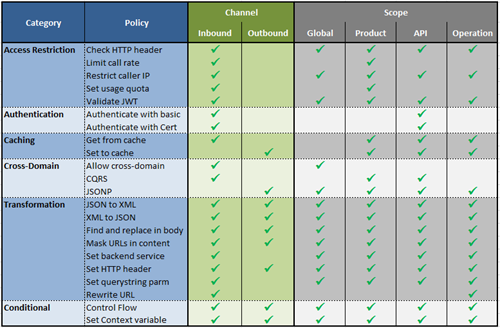
The Policies that are defined at different scopes are then pulled from the higher level to the lowest through the “<base/>” element and flattened to a single policy definition that executes the steps in a sequence.
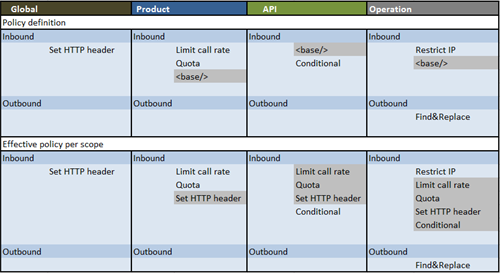
Here the definition of the policies I setup for this blog post and the effective result per scope.
Conditional policies
On April 10th conditional policies have been rolled out:
- Policy expressions. C#-based expressions that can be used as values in policy attributes and elements.
- Control flow policy. That’s an if-then-else construct to conditionally apply policies based on the evaluation of logical expressions.
- Set variable policy. Use this policy to store a computed value for later re-use within the scope of a single request.
- Set backend service policy. To override the backend service URL.
The conditional policies bring flexibility to the API Management policy engine enabling the definition of more complex complex rules like evaluate headers in the inbound pipeline, save it in the context and then, based on that properties, take decisions on the outbound channel.
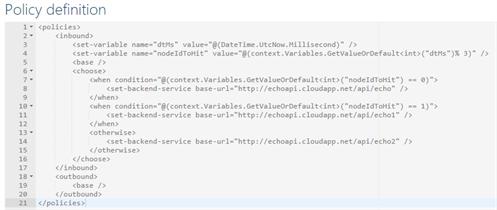
In the very basic example below I combined these 4 new policies in a single policy definition to route the request message to different endpoints depending on the datetime millisecond.
Test and analyze the trace
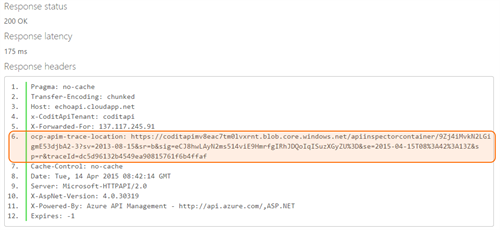
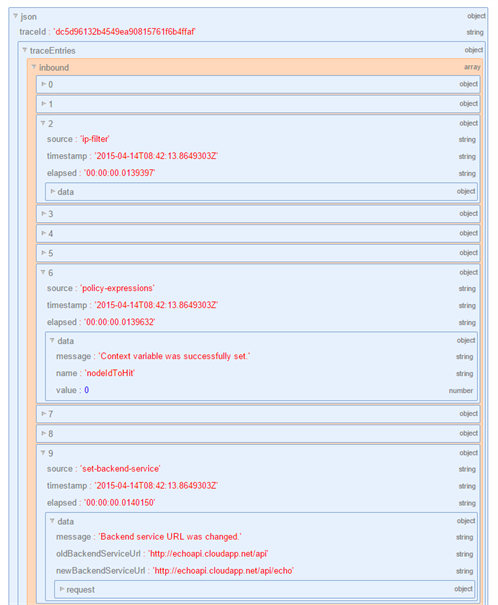
To test the policy definition I used the API management built-in console and I added the “ocp-apim-trace:true” header to the operation call to enable the API inspector.
The trace location is returned in the response ocp-apim-trace-location header which can be used to download the json data to inspect the execution.
Here I got the json using fiddler and then the online json visualizer to easily inspect the trace, check the policy execution and the debug messages.
With the Azure API Management policies you gain the ability to protect, transform and to modify the underlying behavior of the virtualized backend service.
The April service update and the conditional policies brought more flexibility and power to the policy engine.
Cheers
Massimo
Subscribe to our RSS feed