Building Landing Zones
-
build your own bicep modules.
-
use the Common Azure Resource Modules Library (aka CARML https://aka.ms/carml), a library of mature bicep modules curated by Microsoft.
-
One or multiple modules for the networking, one module per supporting support services, application modules, etc.
-
The modules normally contain a set of resource definitions.
-
Modules are then called in the right sequence by bicep orchestration files.
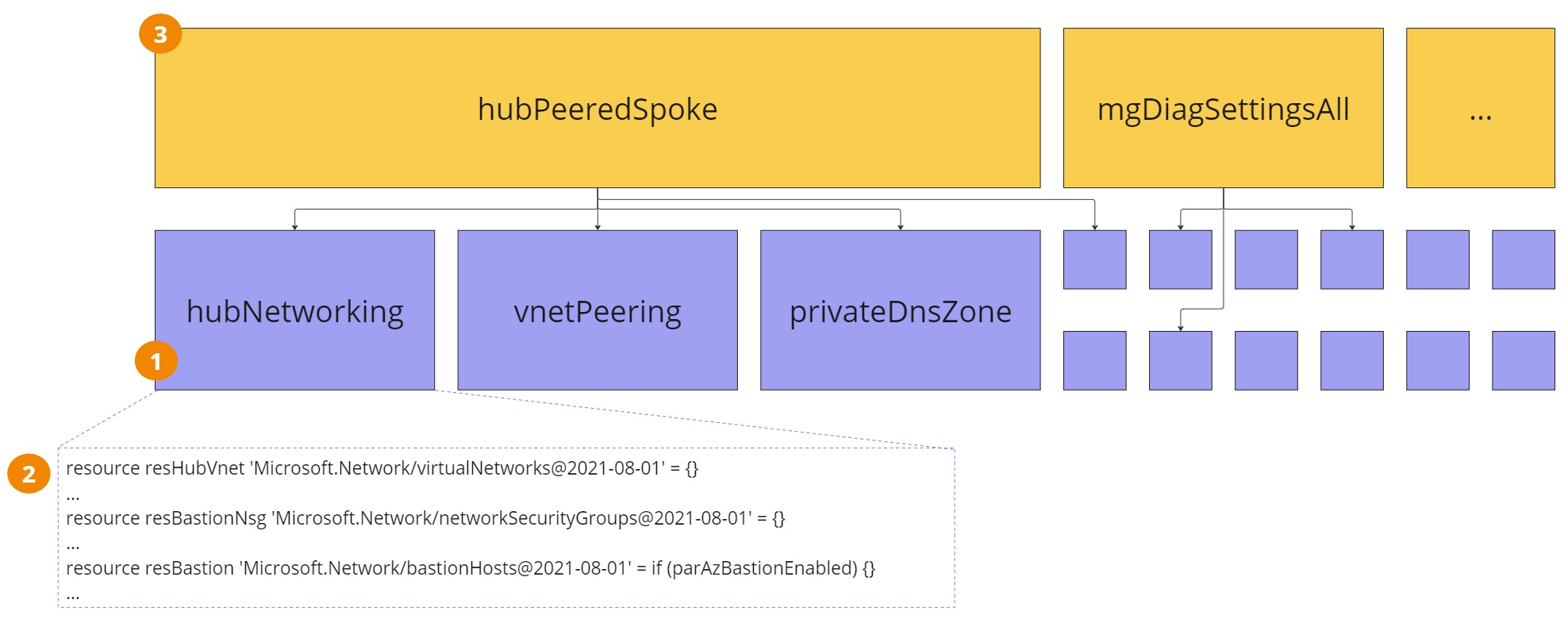
Leveraging the CARML
-
One orchestrator per subscription (Management, Connectivity, Identity, Sandbox, etc.) plus one orchestrator for the management group creation and subscription placement. Basically, this means having one orchestrator per design area for Enterprise-scale landing zones.
-
Multiple bicep modules to assemble the CARML modules in a reusable way. In this way, I can design chunks of the architecture.
-
A multitude of the CARML modules curated by Microsoft. Each CARML module is tied to a specific resource type (virtualNetwork, ipGroup, routeTable, etc.) and grouped by resource providers (Microsoft.Network).
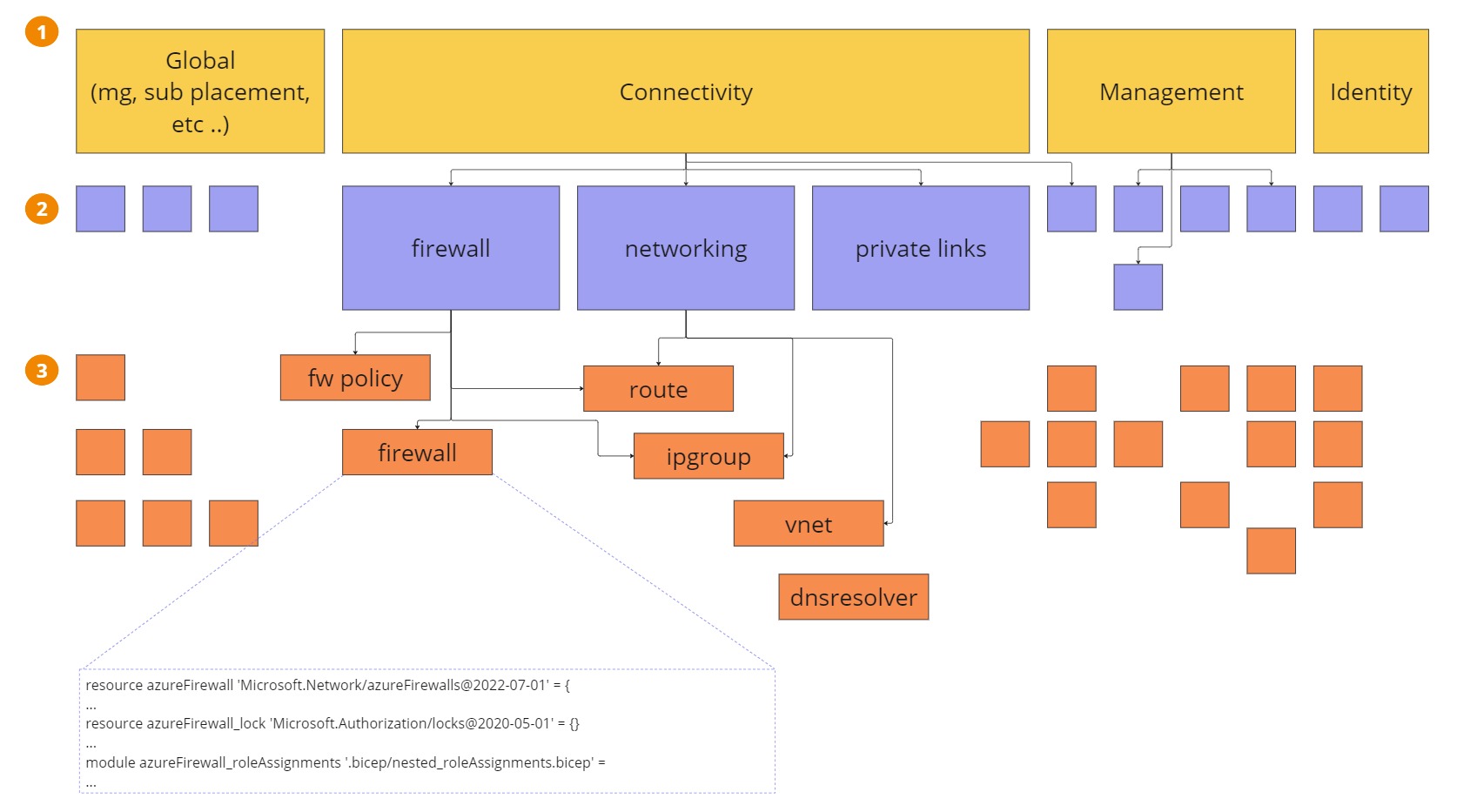
Share the CARML modules
-
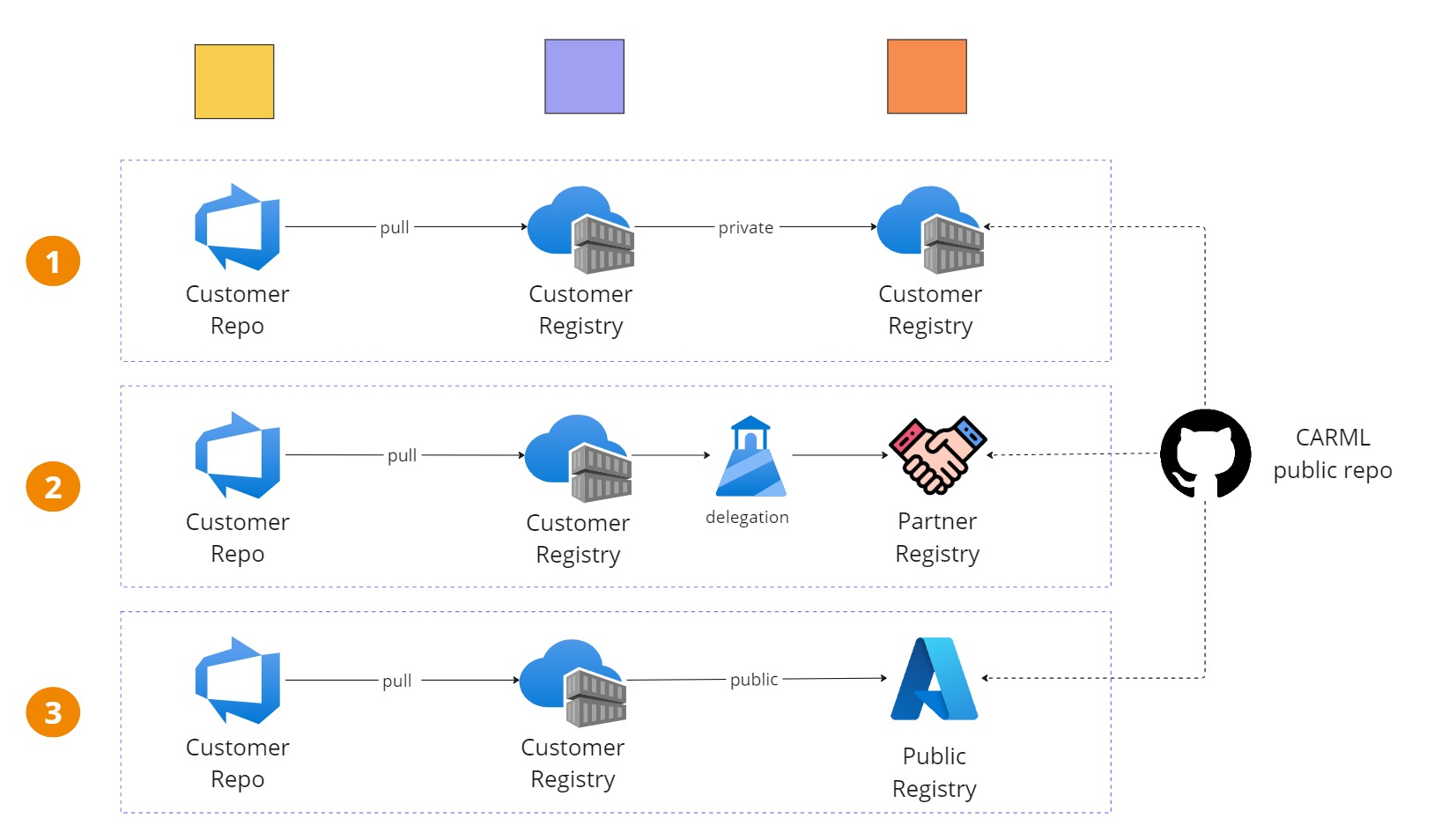
leverage the Azure RBAC and provide access to the proper identities by assigning push and pull permission to the ACR.
-
reference your modules with an intuitive syntax (e.g. module modNetworkWatcher ‘br/networking:watcher:1.0.epsilon’ ={} )
-
reduce the external dependencies.
-
The use of the public registry is the simplest and the cheapest solution. If that external dependency works for you, you can begin quickly. If you need to deviate to the CARML, you can build your own version and push it to the customer registry. Unfortunately, at the time of writing a limited number of modules are available.
-
Publishing the CARML on the customer private registry makes the security tighter, but you have to put a procedure in place to maintain the CARML, intake a new version, and make sure you have a deprecation strategy. That’s not an easy procedure: the cloud is moving fast, and new services are popping up at the same pace as deprecations.
-
A better solution might be to delegate the maintenance of a registry to a partner and use the Azure Lighthouse to grant access to the partner registry. The partner will take care of introducing new features when needed, such as upgrades, deprecations, and more. This guarantees peace of mind, along with a fully managed service.
Conclusion
Subscribe to our RSS feed