How to onboard your APIs
Onboarding APIs to the Defender is fairly simple. Before you can onboard an actual API however, a few steps are necessary. Firstly, you need to register the `Microsoft.APISecurity` Resource Provider for your subscription(s). This might take a few minutes, but once the provider shows up as registered, you will need to enable Defender for APIs on your Azure subscription (Microsoft Defender for Cloud > Environment settings > your subscription > Defender plans).
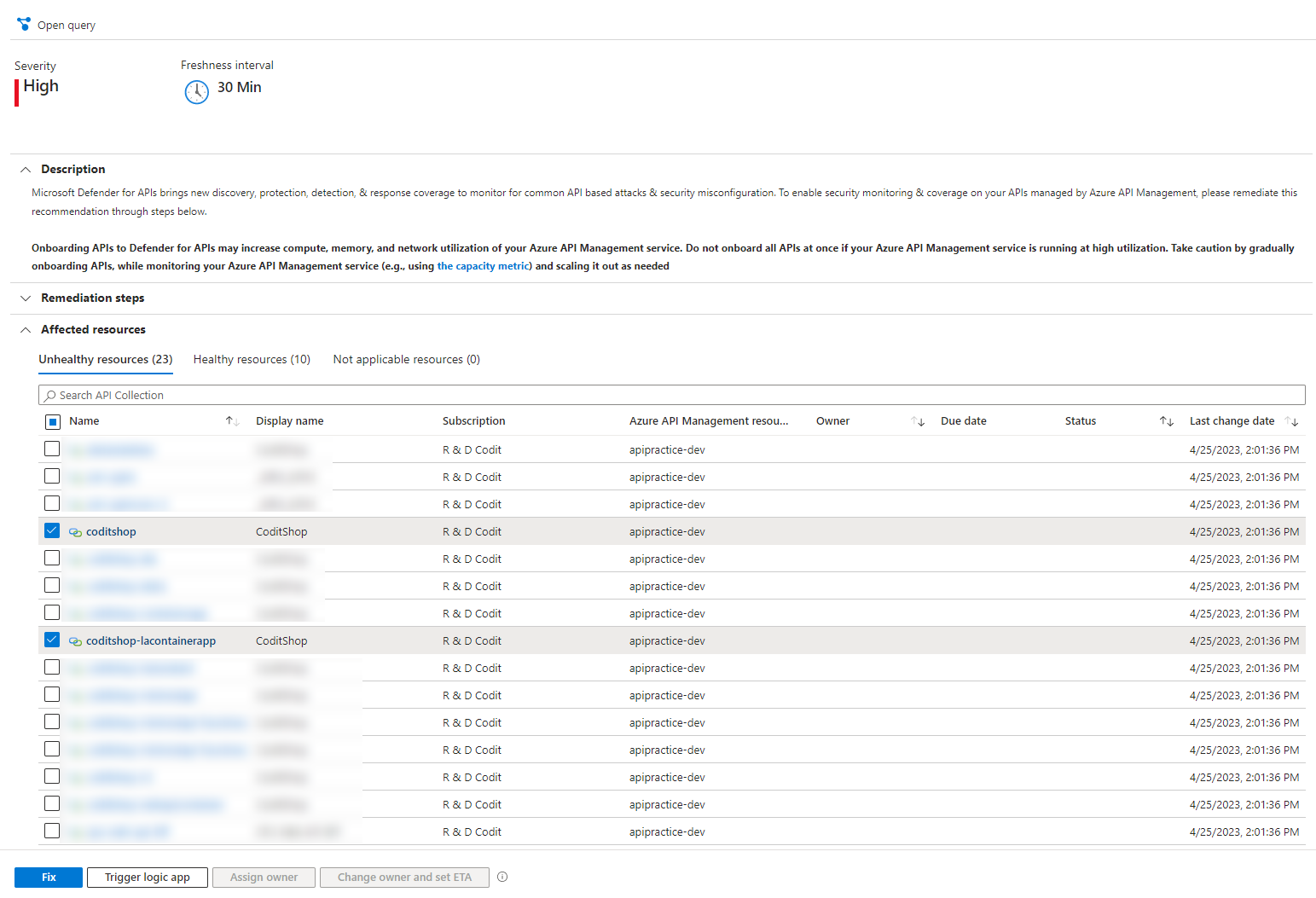
As part of the onboarding procedure, the Defender will go over the APIs to detect all the endpoints (operations) hosted by the selected APIs. Next to that, the API Management traffic is transparently mirrored to Defender in order to build an understanding of how the APIs are used and what kind of information is passing through.
What the solution has to offer
Inventorization
Detection and alerting
The solution is backed by Machine Learning and this comes with some great benefits. The Defender will analyze the traffic going to the API and the request content. By doing so, the solution can provide ML-based detections and address security breaches or incoming attacks next to the OWASP API risks. For example, if the load on a certain endpoint for a particular IP is drastically higher than what is usually expected, an alert would be raised. The alerts are visible within the Microsoft Defender for cloud and give a proper overview of which resource is affected, as well as details about the endpoint and caller.
- Uncommon payload size coming from a single IP to an API endpoint
- Suspicious spike in API latency between single IP and an API endpoint
- Uncommon parameter used towards your API endpoint
- Parameter enumeration
Insights
APIs allow different software applications to interact and exchange information, enabling the creation of complex and integrated systems. However, as APIs become more prevalent and widely used, they also become a prime target for cyber attacks.
In order to secure APIs and protect against potential security threats, it is important to have a deep understanding of API security. Insights in API security can help developers and in this case, non-technical people, to identify and address vulnerabilities. Without proper security measures, APIs can be vulnerable to things such as injection attacks, broken authentication and authorization, and cross-site scripting. Therefore, gaining insights into API security is crucial for any organization that wants to ensure the confidentiality, integrity, and availability of its data and systems.
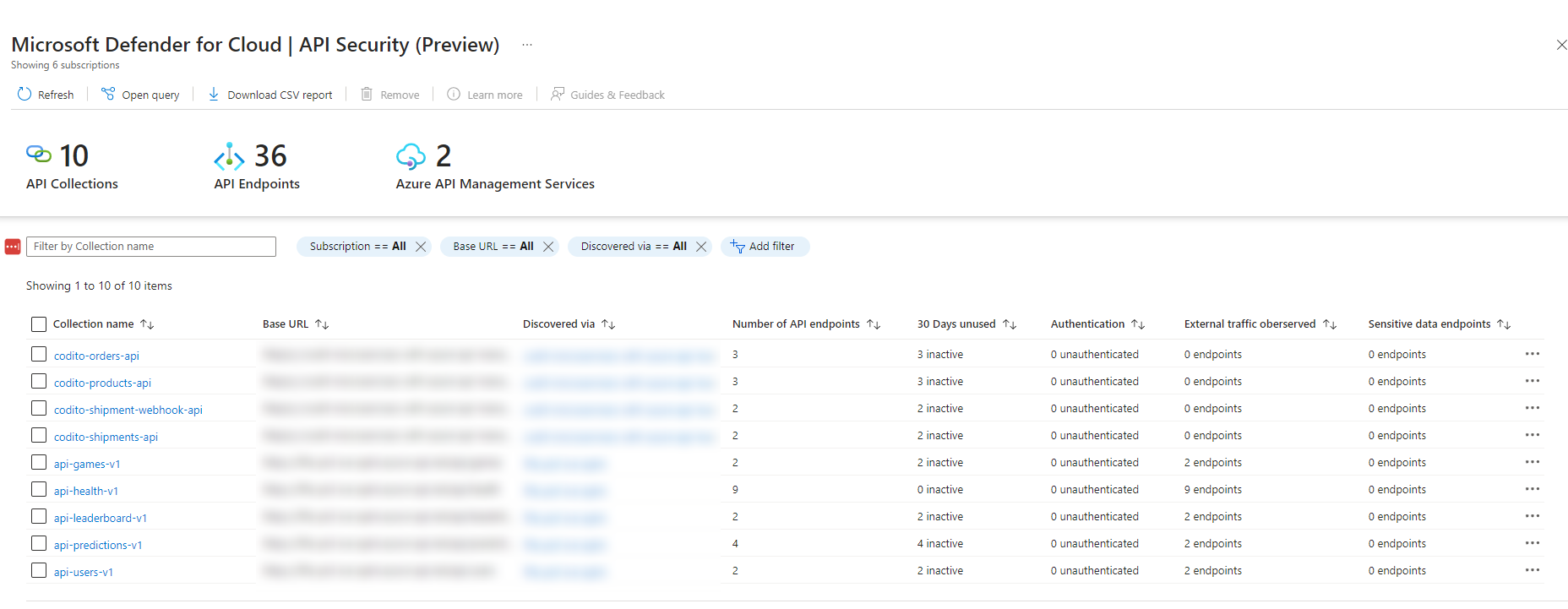
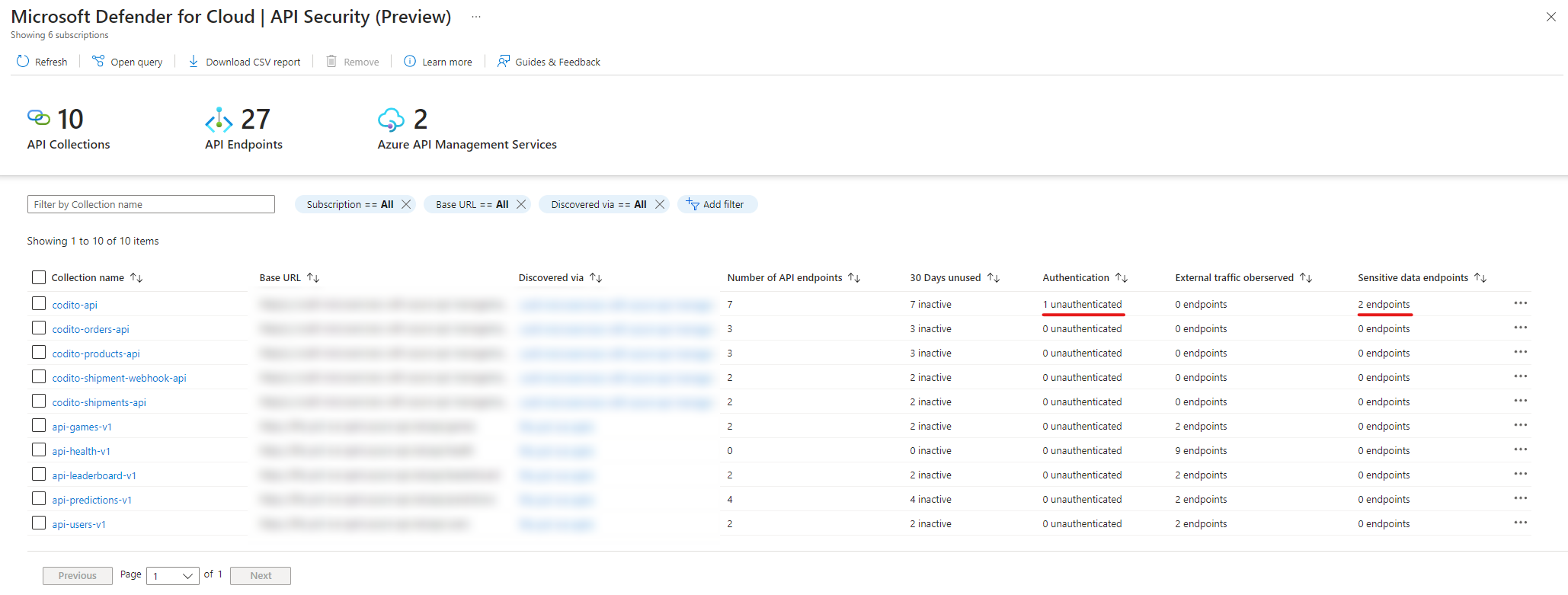
- if there are any sensitive data or unauthenticated endpoints;
- the number of API endpoints within the collection;
- in which API Management service the collection was discovered;
- the number of inactive endpoints (these are endpoints that are not used within 30 days);
- if there is any external traffic observed.
Why use this solution?
Subscribe to our RSS feed