Azure Container Registry (ACR)
Azure Container Registry (ACR) is a fully managed private Docker container registry that enables you to store, manage, and deploy your container images. However, securing container workflows can be a complex task, especially when dealing with sensitive data and multiple teams. Here, we will discuss some best practices and features that you can use to secure your container workflows on ACR. Security should be integrated as an essential part of your continuous integration/continuous delivery (CI/CD) pipeline, and everyone involved should be aware of their role and responsibility in maintaining security.
- Implement security in your pipeline: Implement security gates in your pipeline to ensure that only images that pass security checks are deployed. With open-source tools such as the Image Scan Automation Enrichment Security Gate tool, vulnerability checks and scans can be easily integrated.
- Regularly scan images for vulnerabilities: Container images can contain vulnerabilities that could be exploited by attackers. Microsoft Defender for Cloud can be used to scan images continuously and push and pull.
- Use Private Links: Azure Container Registry (ACR) private links provide a secure and scalable way to access your container registry over Azure Private Link. It enables you to access your ACR resources privately from your virtual network (VNet) and on-premises networks, without the need for a public IP or a VPN. You can also use Azure Private Link to access your ACR from on-premises networks.
- Use Customer Managed Keys: By using customer-managed keys, you can have more control over the encryption and decryption process, which helps to protect your data from potential threats, such as data breaches. Additionally, you can also use Azure Key Vault to manage the lifecycle of your keys, such as rotating them on a regular basis.
- Use Docker Content Trust: This is a feature that allows you to ensure the authenticity and integrity of your container images. It uses digital signatures to verify that an image has not been tampered with and comes from a trusted source. You can use Azure Key Vault to store your keys and manage their lifecycle, such as rotating them on a regular basis.
Securing Azure Kubernetes Service (AKS)
Azure Kubernetes Service (AKS) is a managed Kubernetes service offered by Microsoft Azure that makes it easy to deploy, manage, and scale containerized applications. While AKS simplifies the management of your Kubernetes cluster, it is important to ensure that your cluster and the applications running in it are secure. This blog post outlines some best practices for securing your AKS cluster.
- Use Role-Based Access Control (RBAC)
RBAC is a built-in feature of Kubernetes that allows you to control who has access to your cluster and what actions they can perform. With RBAC, you can assign roles to users, groups, and service accounts, granting them only the permissions they need to perform their job. For example, you can give a developer access to deploy and manage their applications, but restrict their access to the underlying infrastructure.
- Enable network segmentation
Network segmentation is a security technique that separates different parts of your network into separate subnets, reducing the attack surface and preventing unauthorized access. In AKS, you can use network policies to define the allowed communication between your pods, ensuring that only the necessary communication is allowed.
- Use secrets management
Secrets management is a crucial aspect of security in Kubernetes. Secrets, such as passwords, API keys, and certificates, should be stored securely and managed in a way that minimizes the risk of exposure. In AKS, you can use Azure Key Vault, a cloud-based secrets management service, to securely store and manage your secrets. Key Vault integrates with AKS, allowing you to retrieve secrets at runtime, without having to hardcode them into your application code.
- Monitor and audit your cluster
Monitoring and auditing your AKS cluster is essential for detecting and responding to security incidents. Azure provides several tools for monitoring and auditing your AKS cluster, including Azure Monitor for containers and Azure Log Analytics. These tools allow you to monitor the health and performance of your cluster, and to view detailed logs and metrics for troubleshooting and security analysis.
- Regularly update and patch your cluster
Finally, it is important to keep your AKS cluster up-to-date with the latest patches and updates. This helps ensure that your cluster is protected against the latest security vulnerabilities and threats. Azure automatically applies security patches and updates to the control plane components of your AKS cluster, but it is important to also keep your application components up-to-date.
In conclusion, securing your AKS cluster requires a combination of good practices, including using RBAC, network segmentation, secrets management, monitoring and auditing, and regularly updating and patching your cluster. By following these best practices, you can help ensure that your AKS cluster and applications are secure and protected against potential threats.
Monitoring
Azure Monitor
The scope of Azure Monitor is to aggregate and display (log) data from several resources. Container Insights can be accessed from Azure Monitor as follows:
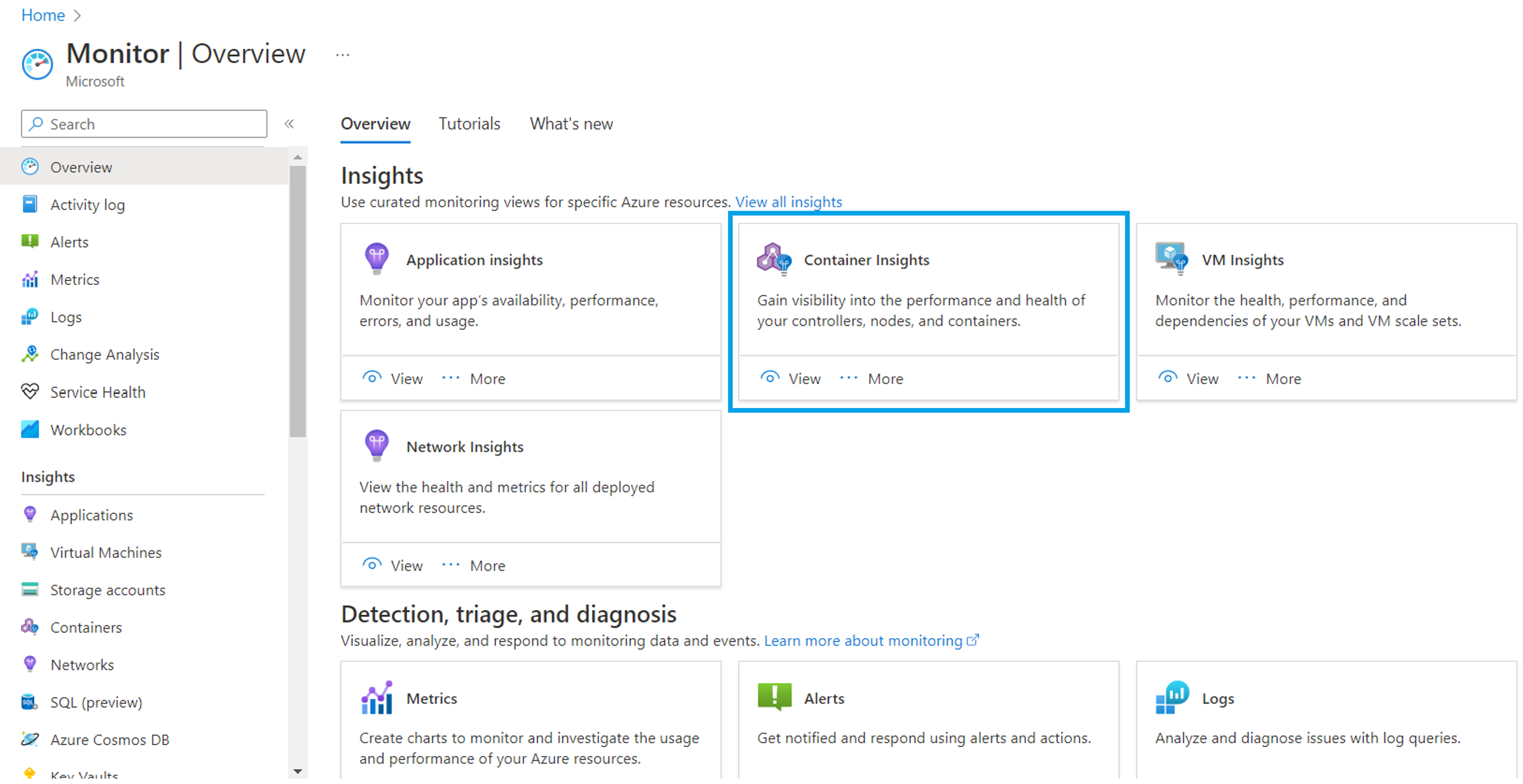
Log Analytics
Log Analytics is used by the container platforms. It is a unique environment for Azure Monitor log data. It is integrated in Azure Monitor and uses the Kusto query language (KQL). Its scope is to collect data from different Azure resources. It can be accessed as follows:
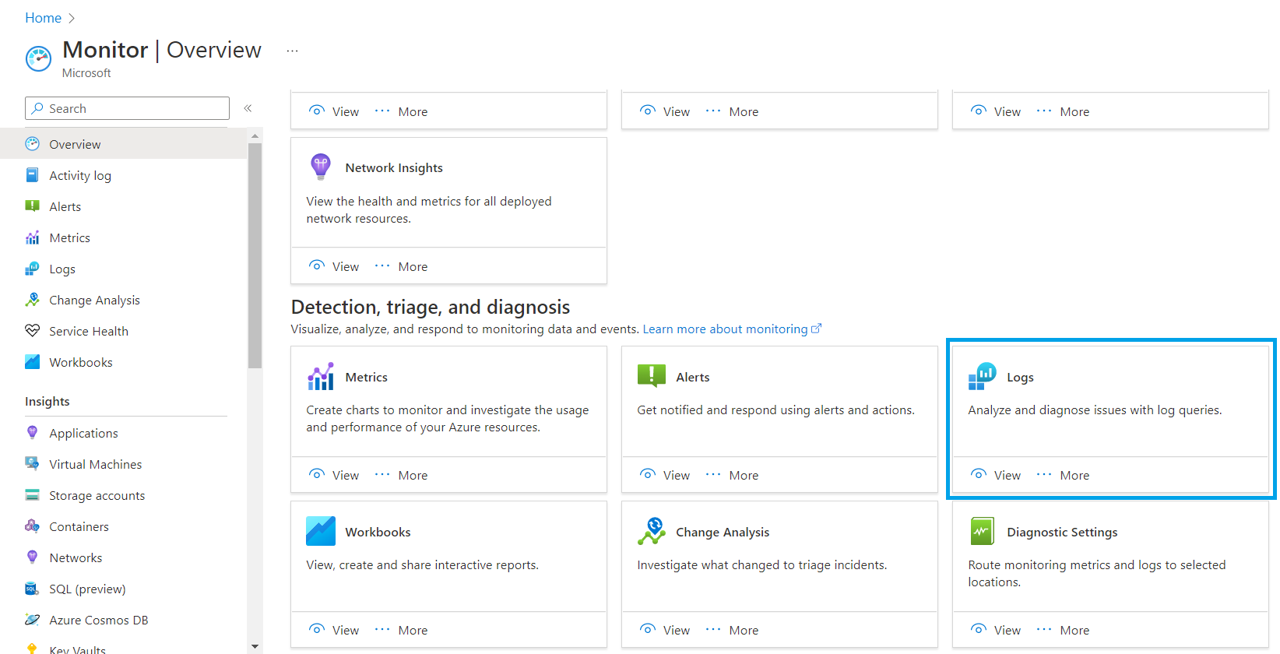
Container Insight
- Previously known as Azure Monitor for Containers.
- Container insights is a feature designed to monitor the performance of container workloads deployed to the cloud.
- It gives you performance visibility by collecting memory and processor metrics from controllers, nodes, and containers that are available in Kubernetes through the Metrics API.
- After you enable monitoring from Kubernetes clusters, metrics and Container logs are automatically collected for you through a containerized version of the Log Analytics agent for Linux.
- Metrics are sent to the metrics database in Azure Monitor.
- Log data is sent to your Log Analytics.
- Container Insights in Azure Monitor is a free service.
A high-level view of the monitored clusters that can be filtered on Subscription and Environment includes:
- Cluster Status Summary – Total Count of Clusters & State.
- Nodes – state of the underlying infrastructure on a per-node basis.
- User Pods – state of the user pods that are deployed related to our own apps.
- System Pods – state of Kubernetes components.
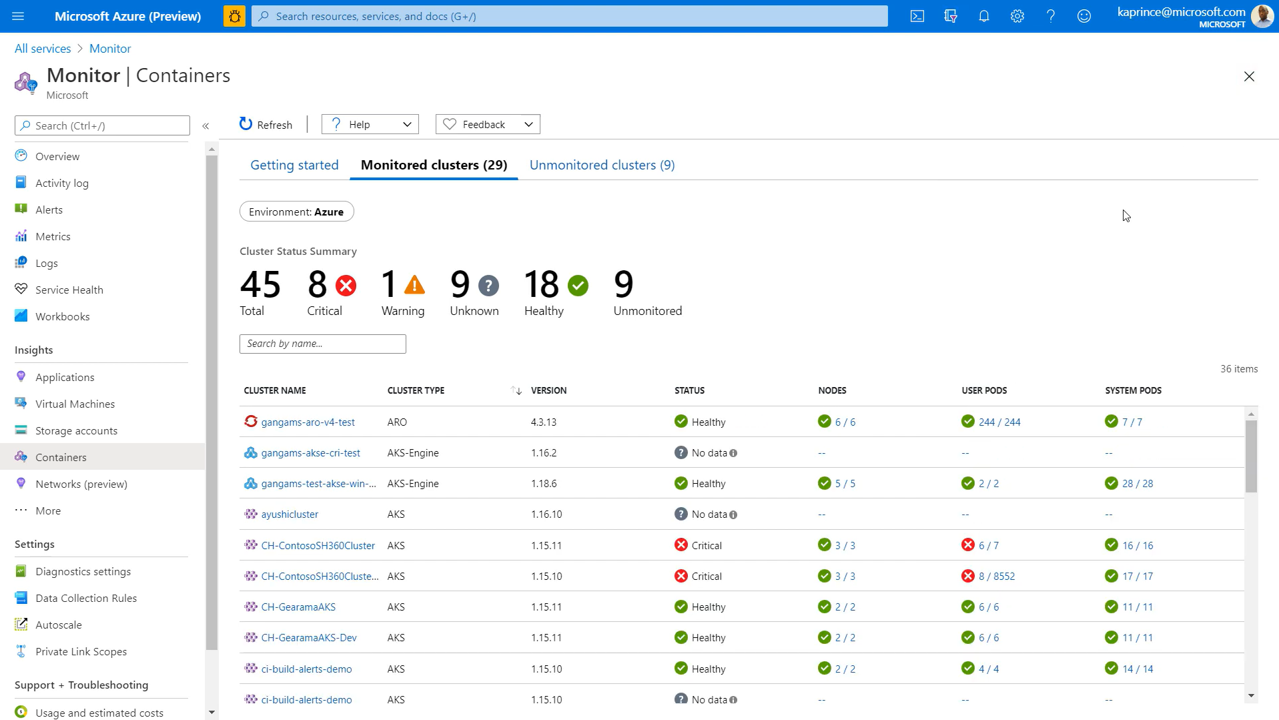
Troubleshooting a problem
Drill into one of the clusters in a critical state:
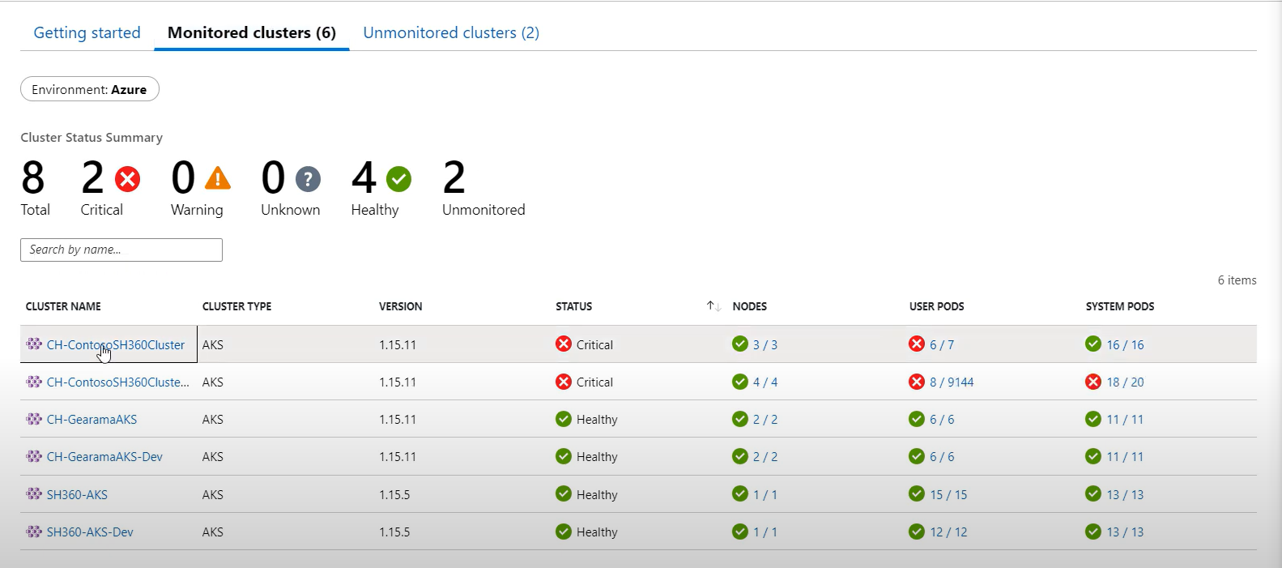
Cluster view:
- CPU & Memory utilization (with relation to scaling operations being performed)
- Node count & Active Pod count (track increases/decreases resulting from autoscaling)
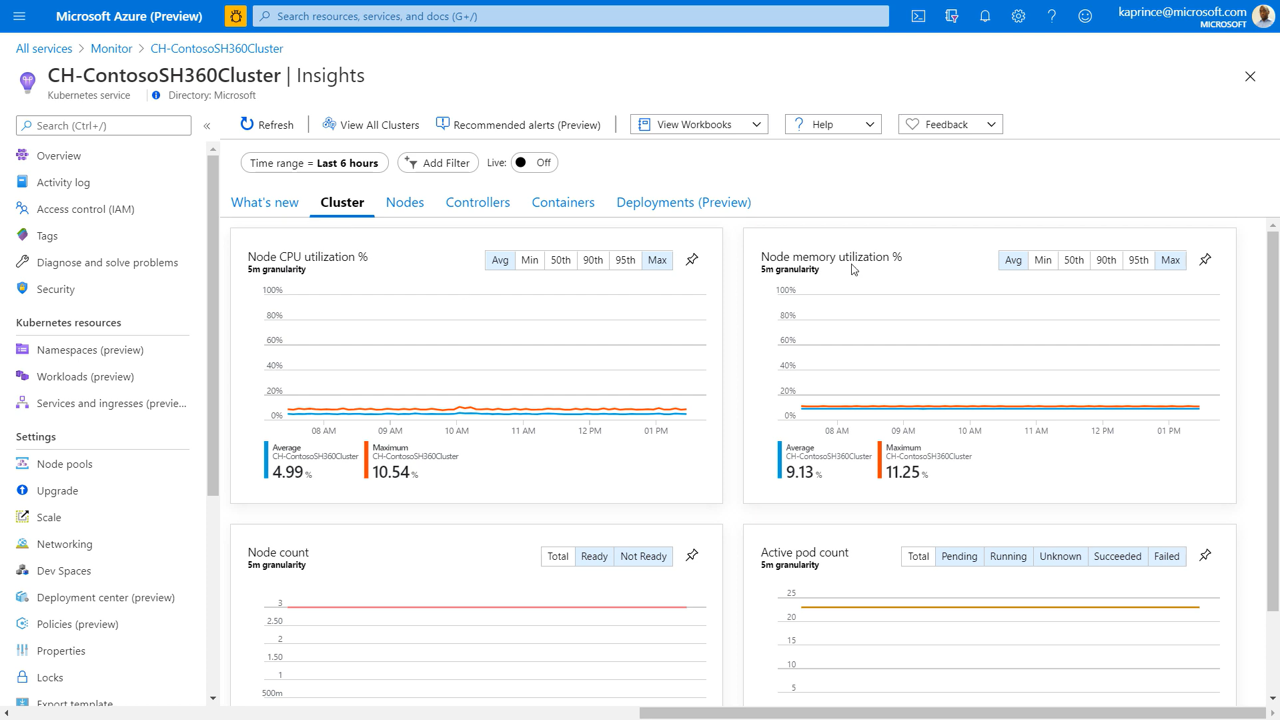
Nodes view:
- Pods and Containers are shown when expanding the Node
- Minecraft container on this node – memory is running hot intermittently
- This may lead to follow on performance issues (which will require further investigation)
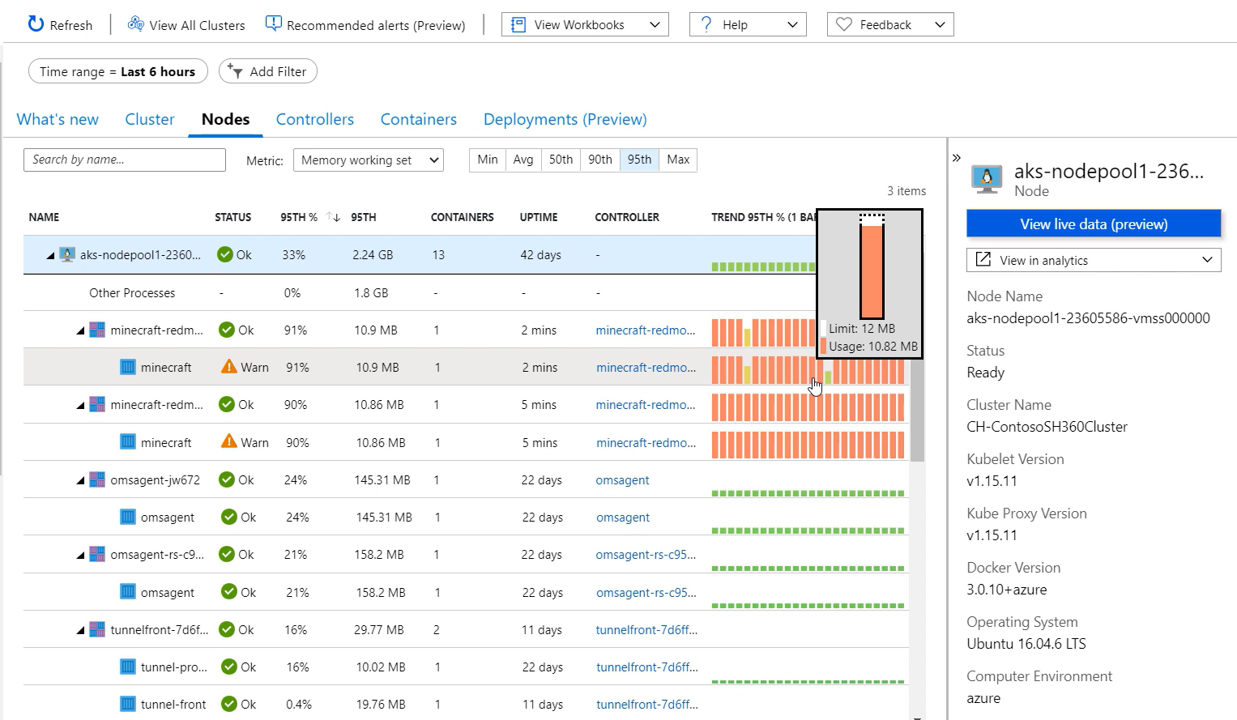
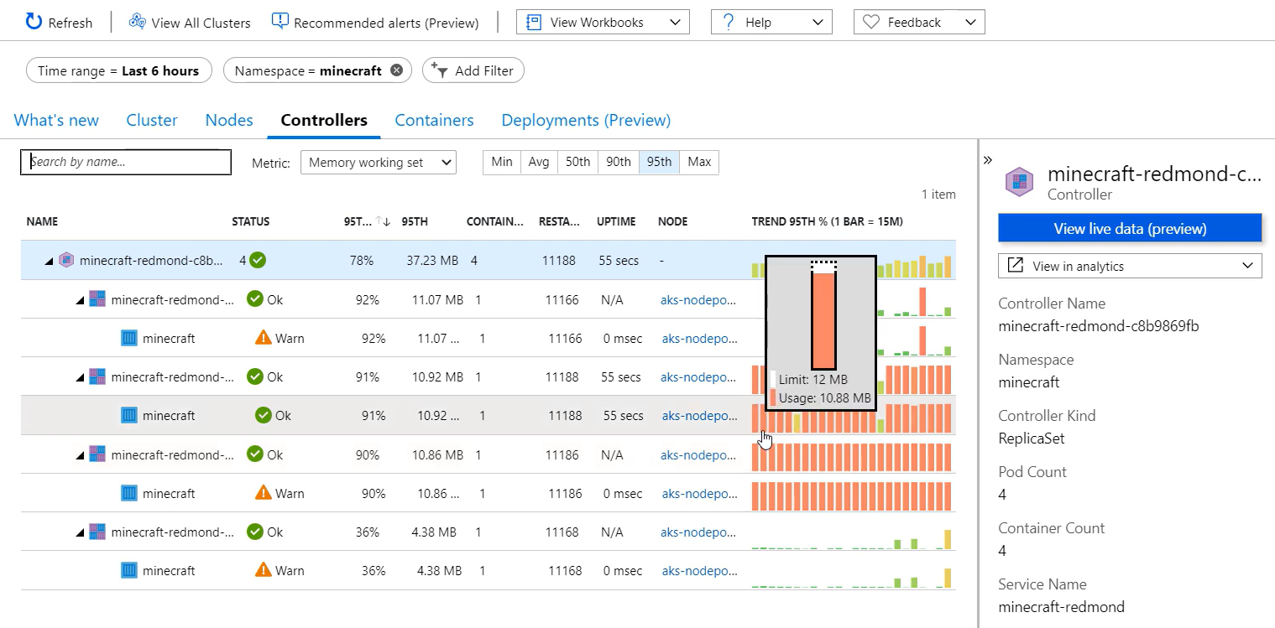
Controllers view:
- The Controller can be expanded to show pods and containers and any related performance metrics;
- For each controller, pod or container – view additional details and associated metadata;
- Same intermittent high memory usage;
- In contrast to this problem being limited to a single node before, the problem is widespread, affecting all of the Container.
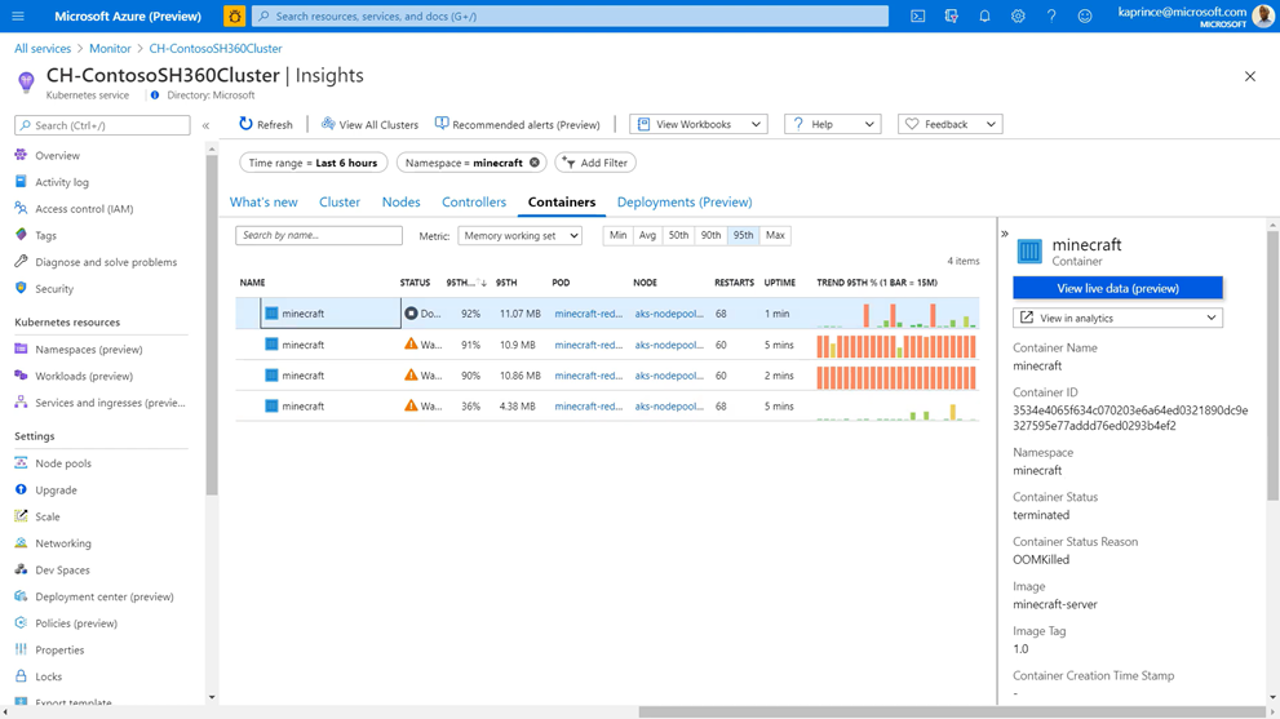
Containers view:
- No tree view – lists each container in a separate row with current state and performance metrics;
- Access to details in the right pain;
- Status is terminated – out of memory termination (OOMKilled);
- g. of Azure Monitor for Containers providing guided troubleshooting by showing changes in state and other anomalies in CPU and Memory metrics.
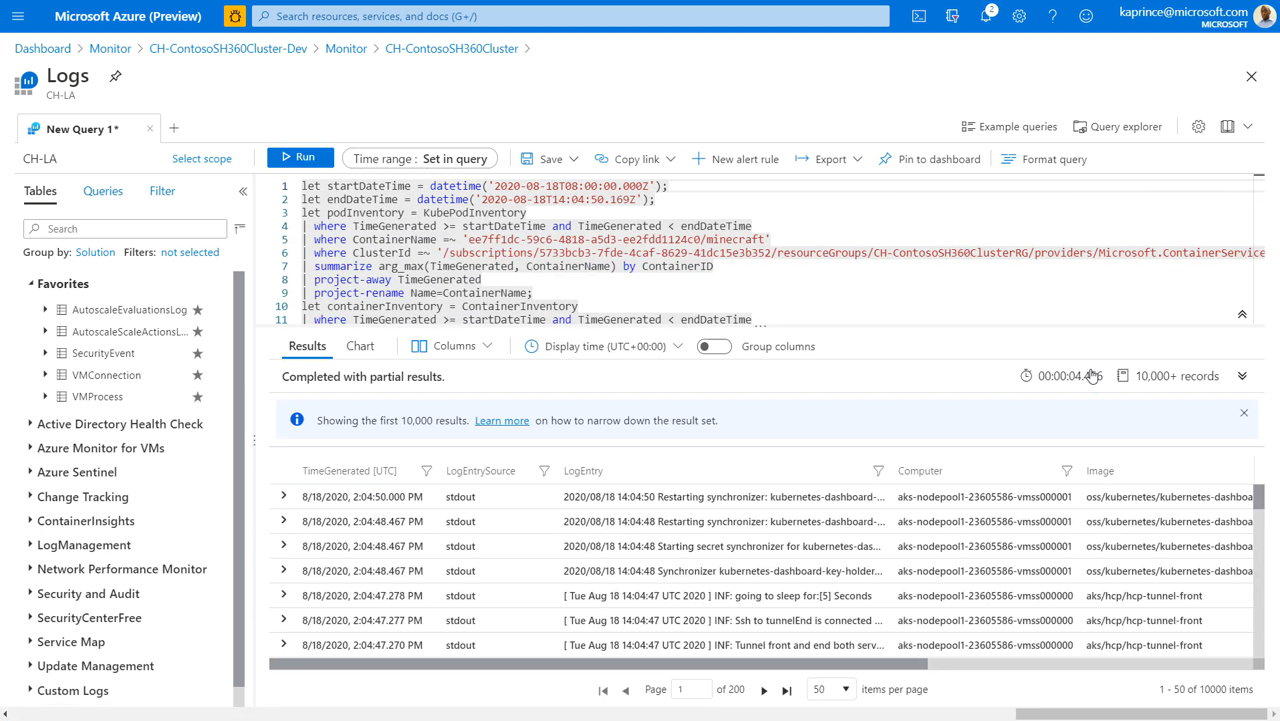
Container Logs:
- Prepopulating workspace selection;
- Query that filters on relevant time range, cluster & container using Kusto query language (KQL);
- Access to all logs generated by the container;
- Can modify further the query;
- Can create New Alert Rules;
- Example Queries are included (on the left).
In summary, Azure Container Services is a powerful platform for building and deploying containerized applications. However, with the flexibility and scalability that containers provide, the need for proper security measures is imperative. By following the best practices and tips discussed in this blog post, you can help to secure your ACS deployments and protect your applications and data.
Subscribe to our RSS feed